 This post is one of a series of blog posts from the first ONA class of MJ Bear Fellows describing their experiences, projects and sharing their knowledge with the ONA community. Fellow Lucas Timmons is a data journalist and web producer for The Edmonton Journal in Edmonton, Alberta, Canada.
This post is one of a series of blog posts from the first ONA class of MJ Bear Fellows describing their experiences, projects and sharing their knowledge with the ONA community. Fellow Lucas Timmons is a data journalist and web producer for The Edmonton Journal in Edmonton, Alberta, Canada.

The Tor logo.
The Tor project website says, “Journalists use Tor to communicate more safely with whistleblowers and dissidents.”
If used properly, Tor can be incorporated into your reporting to keep you and your sources safe. If you’re reporting from a country with Internet censorship laws, it can also help you connect to where you need to go on the Internet.
What does it do?
Tor protects you from Internet stream traffic analysis. Essentially, it makes you anonymous by shielding the content of your data stream from those who would use it to identify you, or things about you, including information about your location. Even if your data is encrypted, traffic analysis still can be used to figure out a lot about what you’re sending and to whom.
How does traffic analysis work? According to the Tor project’s site:
“Internet data packets have two parts: A data payload and a header used for routing. The data payload is whatever is being sent, whether it’s an email message, a web page or an audio file. Even if you encrypt the data payload of your communications, traffic analysis still reveals a great deal about what you’re doing and, possibly, what you’re saying. That’s because it focuses on the header, which discloses source, destination, size, timing and so on.”
Any information that can identify you or your source should be guarded as closely as possible. Just dealing with encryption isn’t enough.
How can I use it?
Journalists can use Tor for many different purposes, including identity protection of sources and journalists and to aid in publishing.
How are reporters using Tor?
- Reporters without Borders tracks Internet prisoners of conscience and jailed or harmed journalists all over the world. They advise journalists, sources, bloggers and dissidents to use Tor to ensure their privacy and safety.
- The U.S. International Broadcasting Bureau (Voice of America/Radio Free Europe/Radio Free Asia) supports Tor development to help Internet users in countries without safe access to free media. Tor preserves the ability of persons behind national firewalls or under the surveillance of repressive regimes to obtain a global perspective on controversial topics including democracy, economics and religion.
- Citizen journalists in China use Tor to write about local events to encourage social change and political reform.
- Citizens and journalists in Internet black holes use Tor to research state propaganda and opposing viewpoints, to file stories with non-State controlled media and to avoid risking the personal consequences of intellectual curiosity
Information provided by The Tor Project
When dealing with sensitive sources, anonymity can be crucial. By using Tor, journalists can ensure that all online discussions and the transfer of files with sources remain anonymous. Going through Tor also will shield you and your source’s IP addresses, so if a news outlet is compelled by the government to turn over communication logs, the source’s online identity still will be protected.
Journalists who wish to remain anonymous also can use the service to keep safe while working in countries with less friendly press laws. Tor will shield what you are looking at and allow access to blocked sites online. For example, if the jurisdiction you are in prevents Facebook access, using Tor enables you to visit Facebook. This can be incredibly helpful if you are trying to publish news and your platform has been blocked by government web filters. Tor also is the perfect solution if you have access to your publishing platform, but want to hide where you are posting from.
A great example of why IP / location protection is important happened recently in Canada. Someone had created an anonymous Twitter account — Vikileaks30 — to leak embarrassing information about federal cabinet minister Vic Toews.
To find out who the tweeter was, the Ottawa Citizen created a web page and emailed the link to the owner of the Vikileaks30 account. The link was opened by the tweeter and because he visited the page, his IP address had been recorded by the Ottawa Citizen.
It turns out the IP address came from a computer in the House of Commons. After a brief internal investigation, the owner of the account was identified as an opposition party staffer. He was fired, and the Liberal party was forced to apologize. If he had been using Tor, his identity would have been shielded.
If a newspaper can do this, there’s no question governments can.
So how does Tor work?
Tor uses a network of proxies to connect you and your destination. It takes your data and runs it through three different servers going to the computer you connect to. To keep this anonymous, none of the servers know the entire route between you and the computer you’re connecting to. No one watching will be able to tell where your data is going to or where it’s coming from. Tor describes this type of connection as “using a twisty, hard-to-follow route in order to throw off somebody who is tailing you — and then periodically erasing your footprints.”
Tor creates a private network pathway for you to use to connect to your desired location. It does this through relays. Each relay in the network knows only where it’s getting data from and where it’s sending data to. No relay will know the full path that your data has taken. The transfer between each relay is also encrypted with a different key.
Once you’ve established a connection, you can safely send data over the Tor network. Traffic analysis will not reveal any useful information because there is no direct link between the source and the destination. The circuit lasts for about 10 minutes. After that a new one will be created, and your traffic will be routed through it.
How do I set it up?
Setting up Tor is a fairly simple process. Navigate to the Tor project download page and download the Tor bundle. It runs on Windows, OS X or Linux, and can be kept on a USB thumb drive so that you can use it with any computer. The package includes a preconfigured browser (based on Firefox) that you can use to browse the web anonymously.
You also can download the source code and compile it yourself if you don’t trust the package. You will need to configure your browser to use Tor properly if you choose this option.
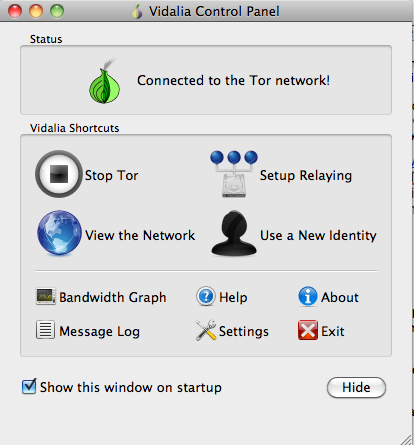
The Tor launcher shows when you are connected to the network.
If you choose to download the bundle, just run the executable inside. It will start the Tor launcher and open a Firefox browser. Once the launcher says, “Connected to the Tor network!” you are ready to go. Remember, for it to work, you need to be using the browser that the bundle provides.
Anything else I should know?
Tor will only make the actual data transfer itself (TCP-stream) anonymous. What you do online and the applications you use could still be unsecured and revealing. For example, the software you use while browsing might identify you. Java, Active X, JavaScript and other extensions can reveal your location, operating system, plugins and a lot more. Your browser also could be improperly configured and still allow outbound connections to look up DNS names without using Tor. This would reveal your location.
You also need to exercise caution when being anonymous. Don’t put your name into online forms. Don’t reveal information about yourself online. Use the secure (HTTPS) versions of sites and not the standard ones.
Conclusion
You may not need to use it all the time, but when you do need anonymity, Tor is a solution worth considering. The laws regarding the Internet are changing, and freedoms are being threatened. Tor is another valuable tool — one that helps working journalists stay anonymous.
